Zeus Trojan Author Ran With Spam Kingpins:
The cybercrime underground is expanding each day, yet the longer I study it the more convinced I am that much of it is run by a fairly small and loose-knit group of hackers. That suspicion was reinforced this week when I discovered that the author of the infamous ZeuS Trojan was a core member of Spamdot, until recently the most exclusive online forum for spammers and the shady businessmen who support the big spam botnets.
Thanks to a deep-seated enmity between the owners of two of the largest spam affiliate programs, the database for Spamdot was leaked to a handful of investigators and researchers, including KrebsOnSecurity. The forum includes all members’ public posts and private messages — even those that members thought had been deleted. I’ve been poring over those private messages in an effort to map alliances and to learn more about the individuals behind the top spam botnets.
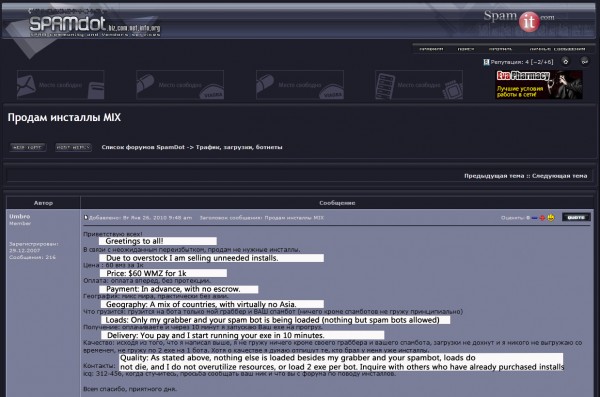
The Zeus author's identity on Spamdot, selling an overstock of "installs."
As I was reviewing the private messages of a Spamdot member nicknamed “Umbro,” I noticed that he gave a few key members his private instant message address, the jabber account bashorg@talking.cc. In 2010, I learned from multiple reliable sources that for several months, this account was used exclusively by the ZeuS author to communicate with new and existing customers. When I dug deeper into Umbro’s private messages, I found several from other Spamdot members who were seeking updates to their ZeuS botnets. In messages from 2009 to a Spamdot member named “Russso,” Umbro declares flatly, “hi, I’m the author of Zeus.”
Umbro’s public and private Spamdot postings offer a fascinating vantage point for peering into an intensely competitive and jealously guarded environment in which members feed off of each others’ successes and failures. The messages also provide a virtual black book of customers who purchased the ZeuS bot code.
In the screen shot above, the ZeuS author can be seen selling surplus “installs,” offering to rent hacked machines that fellow forum members can seed with their own spam bots (I have added a translation beneath each line). His price is $60 per 1,000 compromised systems. This is a very reasonable fee and is in line with rates charged by more organized pay-per-install businesses that also tend to stuff host PCs with so much other malware that customers who have paid to load their bots on those machines soon find them unstable or unusable. Other members apparently recognized it as a bargain as well, and he quickly received messages from a number of interested takers.
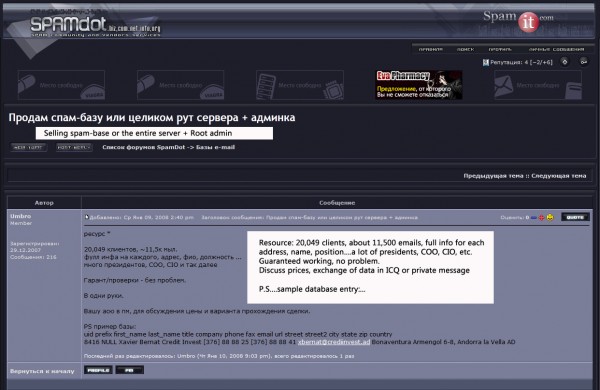
The image below shows the Zeus author parceling out a small but potentially valuable spam resource that was no doubt harvested from systems compromised by his Trojan. In this solicitation, dated Jan. 2008, Umbro is selling a mailing list that would be especially useful for targeted email malware campaigns.
It is not surprising that the Zeus author would frequent such a forum; he is well known to have hung out on other exclusive forums where like-minded cyber thieves set up shop. But Umbro’s messages provide the best proof so far that not only was he the author and main proprietor of a sophisticated Trojan that has helped to steal hundreds of millions of dollars from small to mid-sized businesses, but he also maintained his own sizeable botnets.
Spamdot records show that as often as he sold installs, Umbro turned to some of the top botnet authors to rebuild his private botnets. In an April 14, 2010 private message sent to Ger@ — a Spamdot member I identified earlier this month as the miscreant in charge of the massive Grum botnet — Umbro says he is “ready to buy installs,” and prepared to offer a fair price for buying in bulk. In another communication near that same time, Umbro seeks to rent botnet resources from a business partner of “Google,” the nickname of the individual I identified in January as the author of the Cutwail botnet.
Umbro’s public and private communications reveal how frequently he changed his nicknames, email addresses and other contact details — a common tactic used to confuse and elude law enforcement investigators. By the time Spamdot was closed in Sept. 2010, the ZeuS author was using the nickname “Slavik.” He had just announced that he would be bowing out of the business, and that the code that powers his Trojan would be merged with that of SpyEye.
Security researchers at RSA made an interesting discovery at about the same time the ZeuS author was plotting his final disappearing act. They found evidence that the ZeuS author didn’t exactly retire, but rather appears to have gone into the botnet business for himself. RSA’s Uri Rivner said that just before that merger was announced on underground forums, RSA investigators stumbled upon a botnet created in Aug. 2010 with a custom version of ZeuS that was not being sold or distributed in the underground.
That custom version, which RSA dubbed “ZeuS 2,” phoned home to a control server on the Web that the researchers were able to access. They found that between Aug. 2010 and Aug. 2011, more than 200,000 PCs had phoned home to that server, which had helped vacuum up tens of gigabytes of data from host machines. They also learned that miscreants had created four logins that were authorized to access the botnet’s control server: “rootadmin,” “NS,” “chingiz,” and “Slavik” (see screenshot below).
“This ZeuS2 had a lot of improvements, and was created before the ZeuS source changed hands,” RSA’s Rivner told me in an interview last October. “It might be that Slavik decided to move away from selling software and supporting all of his customers to developing infrastructure that can be rented and becoming part of a larger organized crime group.”
According to a security researcher who has access to the same server but asked to remain anonymous, there are now more than a quarter-million PCs compromised by this custom version of ZeuS and reporting home to that same control server.
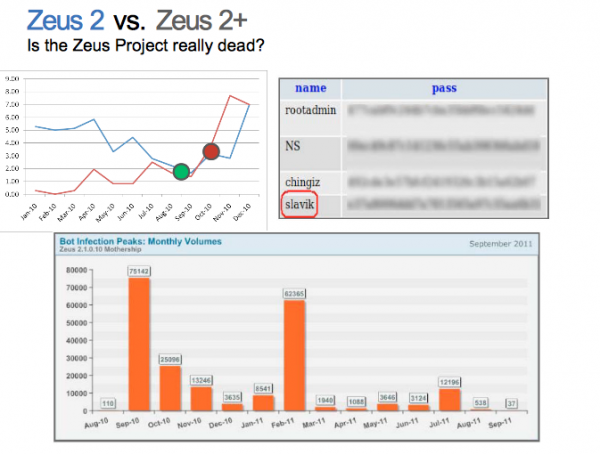
The ZeuS author's nickname 'Slavik' was among those authorized to log into the unusual ZeuS2 botnet.

The cybercrime underground is expanding each day, yet the longer I study it the more convinced I am that much of it is run by a fairly small and loose-knit group of hackers. That suspicion was reinforced this week when I discovered that the author of the infamous ZeuS Trojan was a core member of Spamdot, until recently the most exclusive online forum for spammers and the shady businessmen who support the big spam botnets.
Thanks to a deep-seated enmity between the owners of two of the largest spam affiliate programs, the database for Spamdot was leaked to a handful of investigators and researchers, including KrebsOnSecurity. The forum includes all members’ public posts and private messages — even those that members thought had been deleted. I’ve been poring over those private messages in an effort to map alliances and to learn more about the individuals behind the top spam botnets.
The Zeus author's identity on Spamdot, selling an overstock of "installs."
Umbro’s public and private Spamdot postings offer a fascinating vantage point for peering into an intensely competitive and jealously guarded environment in which members feed off of each others’ successes and failures. The messages also provide a virtual black book of customers who purchased the ZeuS bot code.
In the screen shot above, the ZeuS author can be seen selling surplus “installs,” offering to rent hacked machines that fellow forum members can seed with their own spam bots (I have added a translation beneath each line). His price is $60 per 1,000 compromised systems. This is a very reasonable fee and is in line with rates charged by more organized pay-per-install businesses that also tend to stuff host PCs with so much other malware that customers who have paid to load their bots on those machines soon find them unstable or unusable. Other members apparently recognized it as a bargain as well, and he quickly received messages from a number of interested takers.
The image below shows the Zeus author parceling out a small but potentially valuable spam resource that was no doubt harvested from systems compromised by his Trojan. In this solicitation, dated Jan. 2008, Umbro is selling a mailing list that would be especially useful for targeted email malware campaigns.
It is not surprising that the Zeus author would frequent such a forum; he is well known to have hung out on other exclusive forums where like-minded cyber thieves set up shop. But Umbro’s messages provide the best proof so far that not only was he the author and main proprietor of a sophisticated Trojan that has helped to steal hundreds of millions of dollars from small to mid-sized businesses, but he also maintained his own sizeable botnets.
Spamdot records show that as often as he sold installs, Umbro turned to some of the top botnet authors to rebuild his private botnets. In an April 14, 2010 private message sent to Ger@ — a Spamdot member I identified earlier this month as the miscreant in charge of the massive Grum botnet — Umbro says he is “ready to buy installs,” and prepared to offer a fair price for buying in bulk. In another communication near that same time, Umbro seeks to rent botnet resources from a business partner of “Google,” the nickname of the individual I identified in January as the author of the Cutwail botnet.
Umbro’s public and private communications reveal how frequently he changed his nicknames, email addresses and other contact details — a common tactic used to confuse and elude law enforcement investigators. By the time Spamdot was closed in Sept. 2010, the ZeuS author was using the nickname “Slavik.” He had just announced that he would be bowing out of the business, and that the code that powers his Trojan would be merged with that of SpyEye.
Security researchers at RSA made an interesting discovery at about the same time the ZeuS author was plotting his final disappearing act. They found evidence that the ZeuS author didn’t exactly retire, but rather appears to have gone into the botnet business for himself. RSA’s Uri Rivner said that just before that merger was announced on underground forums, RSA investigators stumbled upon a botnet created in Aug. 2010 with a custom version of ZeuS that was not being sold or distributed in the underground.
That custom version, which RSA dubbed “ZeuS 2,” phoned home to a control server on the Web that the researchers were able to access. They found that between Aug. 2010 and Aug. 2011, more than 200,000 PCs had phoned home to that server, which had helped vacuum up tens of gigabytes of data from host machines. They also learned that miscreants had created four logins that were authorized to access the botnet’s control server: “rootadmin,” “NS,” “chingiz,” and “Slavik” (see screenshot below).
“This ZeuS2 had a lot of improvements, and was created before the ZeuS source changed hands,” RSA’s Rivner told me in an interview last October. “It might be that Slavik decided to move away from selling software and supporting all of his customers to developing infrastructure that can be rented and becoming part of a larger organized crime group.”
According to a security researcher who has access to the same server but asked to remain anonymous, there are now more than a quarter-million PCs compromised by this custom version of ZeuS and reporting home to that same control server.

The ZeuS author's nickname 'Slavik' was among those authorized to log into the unusual ZeuS2 botnet.








No comments:
Post a Comment